Two models of iPhone can be hacked, the charging point itself became a gift for hackers
Thomas Roth discovered a way to hack the ACE3 controller through reverse engineering, RF side-channel analysis, and electromagnetic fault injection. Through this process, he was able to reprogram the controller, inject code, and bypass all security checks.
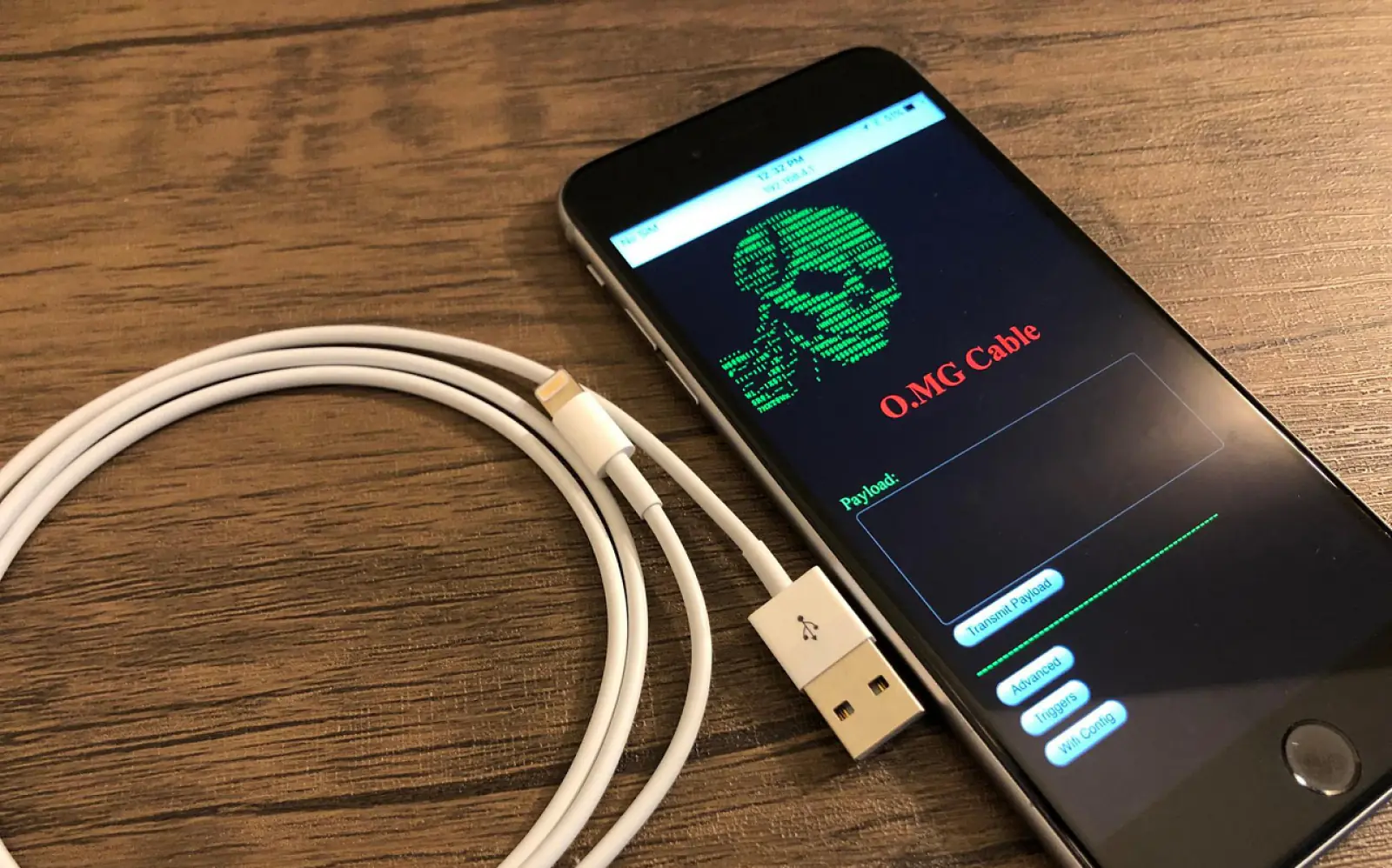
Do you know your iPhone can be hacked if you also have an iPhone and it has a Type-C charging port? What if your iPhone's data goes into the wrong hands just by plugging it into an unknown USB port? The same scary situation is associated with the new USB-C ports and ACE3 USB-C controller introduced with the iPhone 15 and iPhone 16 series. Security researcher Thomas Roth has found a flaw in this charging chip, which could open the door for hackers to hack your phone.
Using reverse engineering, RF side-channel analysis, and electromagnetic fault injection, Thomas Roth discovered it was possible to hack the ACE3 controller, which allowed him to reprogram the controller, inject code, and bypass all security checks.
That means, in case of exploitation by hackers, they gain access to your iPhone and the data in it, though for this they will need physical access, i.e., accessing your phone through a USB-C cable, which is very difficult.
Apple has not yet responded to this flaw. According to security experts, physical access is required to exploit this flaw, which is not a concern for most users. But caution is always necessary.
How to keep your iPhone safe?
- Not on public USB ports: The most important rule - do not charge your phone using unknown USB ports in a coffee shop, at the airport, or some other place with similar amenities.
- Carry a Power bank: It is always a good idea to carry a power bank with you in case of an emergency to charge your phone.
- Avoid Data Transfers: Avoid uploading data on an unknown computer or device.
- Use OTG data blocker: A blocker is to be used with the intent of blocking data access via USB ports.










































































